|
| 1 | ++++ |
| 2 | +title = "BackendTLSPolicy" |
| 3 | ++++ |
| 4 | + |
| 5 | + |
| 6 | + The `BackendTLSPolicy` resource is Alpha and has been part of |
| 7 | + the Experimental Channel since `v1.0.0`. For more information on release |
| 8 | + channels, refer to our [versioning guide](https://gateway-api.sigs.k8s.io/concepts/versioning). |
| 9 | + |
| 10 | +[BackendTLSPolicy][backendtlspolicy] is a Gateway API type for specifying the TLS configuration |
| 11 | +of the connection from the Gateway to a backend pod/s via the Service API object. |
| 12 | + |
| 13 | +## Background |
| 14 | + |
| 15 | +`BackendTLSPolicy` specifically addresses the configuration of TLS in order to convey HTTPS from the Gateway |
| 16 | +dataplane to the backend. This is referred to as "backend TLS termination" and enables the Gateway to know |
| 17 | +how to connect to a backend pod that has its own certificate. |
| 18 | + |
| 19 | +While there are other API objects provided for TLS to be configured for **passthrough** and **edge** termination, |
| 20 | +this API object allows users to specifically configure **backend** TLS termination. For more information on TLS |
| 21 | +configuration in Gateway API, see [TLS Configuration](https://gateway-api.sigs.k8s.io/guides/tls/). |
| 22 | + |
| 23 | +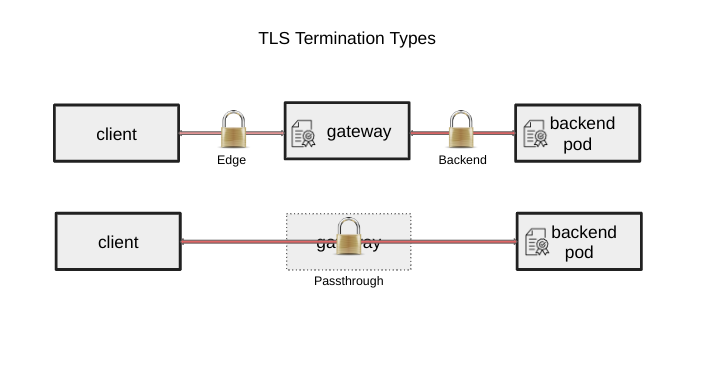 |
| 24 | + |
| 25 | +BackendTLSPolicy is a Direct [PolicyAttachment](https://gateway-api.sigs.k8s.io/reference/policy-attachment/) without defaults or overrides, |
| 26 | +applied to a Service that accesses a backend, where the BackendTLSPolicy resides in the same namespace as the |
| 27 | +Service to which it is applied. The BackendTLSPolicy and the Service must reside in the same namespace in order |
| 28 | +to prevent the complications involved with sharing trust across namespace boundaries. |
| 29 | + |
| 30 | +All Gateway API Routes that point to a referenced Service should respect a configured BackendTLSPolicy. |
| 31 | + |
| 32 | +## Spec |
| 33 | + |
| 34 | +The specification of a [BackendTLSPolicy][backendtlspolicy] consists of: |
| 35 | + |
| 36 | +- [TargetRefs][targetRefs] - Defines the targeted API object of the policy. Only Service is allowed. |
| 37 | +- [Validation][validation] - Defines the configuration for TLS, including hostname, CACertificateRefs, and |
| 38 | +WellKnownCACertificates. |
| 39 | +- [Hostname][hostname] - Defines the Server Name Indication (SNI) that the Gateway uses to connect to the backend. |
| 40 | +- [CACertificateRefs][caCertificateRefs] - Defines one or more references to objects that contain PEM-encoded TLS certificates, |
| 41 | +which are used to establish a TLS handshake between the Gateway and backend Pod. Either CACertificateRefs or |
| 42 | +WellKnownCACertificates may be specified, but not both. |
| 43 | +- [WellKnownCACertificates][wellKnownCACertificates] - Specifies whether system CA certificates may be used in the TLS |
| 44 | +handshake between the Gateway and backend Pod. Either CACertificateRefs or WellKnownCACertificates may be specified, but not both. |
| 45 | + |
| 46 | +The following chart outlines the object definitions and relationship: |
| 47 | +```mermaid |
| 48 | +flowchart LR |
| 49 | + backendTLSPolicy[["<b>backendTLSPolicy</b> <hr><align=left>BackendTLSPolicySpec: spec<br>PolicyStatus: status</align>"]] |
| 50 | + spec[["<b>spec</b><hr>PolicyTargetReferenceWithSectionName: targetRefs <br> BackendTLSPolicyValidation: tls"]] |
| 51 | + status[["<b>status</b><hr>[ ]PolicyAncestorStatus: ancestors"]] |
| 52 | + validation[["<b>tls</b><hr>LocalObjectReference: caCertificateRefs<br>wellKnownCACertificatesType: wellKnownCACertificates/<br>PreciseHostname: hostname"]] |
| 53 | + ancestorStatus[["<b>ancestors</b><hr>AncestorRef: parentReference<br>GatewayController: controllerName<br>[]Condition: conditions"]] |
| 54 | + targetRefs[[<b>targetRefs</b><hr>]] |
| 55 | + service["<b>service</>"] |
| 56 | + backendTLSPolicy -->spec |
| 57 | + backendTLSPolicy -->status |
| 58 | + spec -->targetRefs & validation |
| 59 | + status -->ancestorStatus |
| 60 | + targetRefs -->service |
| 61 | + note[<em>choose only one<hr> caCertificateRefs OR wellKnownCACertificates</em>] |
| 62 | + style note fill:#fff |
| 63 | + validation -.- note |
| 64 | +``` |
| 65 | + |
| 66 | +The following illustrates a BackendTLSPolicy that configures TLS for a Service serving a backend: |
| 67 | +```mermaid |
| 68 | +flowchart LR |
| 69 | + client(["client"]) |
| 70 | + gateway["Gateway"] |
| 71 | + style gateway fill:#02f,color:#fff |
| 72 | + httproute["HTTP<BR>Route"] |
| 73 | + style httproute fill:#02f,color:#fff |
| 74 | + service["Service"] |
| 75 | + style service fill:#02f,color:#fff |
| 76 | + pod1["Pod"] |
| 77 | + style pod1 fill:#02f,color:#fff |
| 78 | + pod2["Pod"] |
| 79 | + style pod2 fill:#02f,color:#fff |
| 80 | + client -.->|HTTP <br> request| gateway |
| 81 | + gateway --> httproute |
| 82 | + httproute -.->|BackendTLSPolicy|service |
| 83 | + service --> pod1 & pod2 |
| 84 | +``` |
| 85 | + |
| 86 | +### Targeting backends |
| 87 | + |
| 88 | +A BackendTLSPolicy targets a backend Pod (or set of Pods) via one or more TargetRefs to a Service. This TargetRef is a |
| 89 | +required object reference that specifies a Service by its Name, Kind (Service), and optionally its Namespace and Group. |
| 90 | +TargetRefs identify the Service/s for which your HTTPRoute requires TLS. |
| 91 | + |
| 92 | + |
| 93 | + - Cross-namespace certificate references are not allowed. |
| 94 | + |
| 95 | +### BackendTLSPolicyValidation |
| 96 | + |
| 97 | +A BackendTLSPolicyValidation is the specification for the BackendTLSPolicy and defines the configuration for TLS, |
| 98 | +including hostname (for server name indication) and certificates. |
| 99 | + |
| 100 | +#### Hostname |
| 101 | + |
| 102 | +Hostname defines the server name indication (SNI) the Gateway should use in order to connect to the backend, and must |
| 103 | +match the certificate served by the backend pod. A hostname is the fully qualified domain name of a network host, as |
| 104 | +defined by [RFC 3986][rfc-3986]. Note the following deviations from the “host” part of the URI as defined in the RFC: |
| 105 | + |
| 106 | +- IP addresses are not allowed. |
| 107 | + |
| 108 | +Also note: |
| 109 | + |
| 110 | + |
| 111 | + - Wildcard hostnames are not allowed. |
| 112 | + |
| 113 | +#### Certificates |
| 114 | + |
| 115 | +The BackendTLSPolicyValidation must contain a certificate reference of some kind, and contains two ways to configure the |
| 116 | +certificate to use for backend TLS, CACertificateRefs and WellKnownCACertificates. Only one of these may be used per |
| 117 | +BackendTLSPolicyValidation. |
| 118 | + |
| 119 | +##### CACertificateRefs |
| 120 | + |
| 121 | +CACertificateRefs refer to one or more PEM-encoded TLS certificates. |
| 122 | + |
| 123 | + |
| 124 | + - Cross-namespace certificate references are not allowed. |
| 125 | + |
| 126 | +##### WellKnownCACertificates |
| 127 | + |
| 128 | +If you are working in an environment where specific TLS certificates are not required, and your Gateway API |
| 129 | +implementation allows system or default certificates to be used, e.g. in a development environment, you may |
| 130 | +set WellKnownCACertificates to "System" to tell the Gateway to use a set of trusted CA Certificates. There may be |
| 131 | +some variation in which system certificates are used by each implementation. Refer to documentation from your |
| 132 | +implementation of choice for more information. |
| 133 | + |
| 134 | +### PolicyStatus |
| 135 | + |
| 136 | +Status defines the observed state of the BackendTLSPolicy and is not user-configurable. Check status in the same |
| 137 | +way you do for other Gateway API objects to verify correct operation. Note that the status in BackendTLSPolicy |
| 138 | +uses `PolicyAncestorStatus` to allow you to know which parentReference set that particular status. |
| 139 | + |
| 140 | +[backendtlspolicy]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1alpha3.BackendTLSPolicy |
| 141 | +[validation]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1alpha3.BackendTLSPolicy.Validation |
| 142 | +[caCertificateRefs]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1alpha3.BackendTLSPolicyValidation.CACertificateRefs |
| 143 | +[wellKnownCACertificates]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1alpha3.BackendTLSPolicyValidation.WellKnownCACertificates |
| 144 | +[hostname]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1.PreciseHostname |
| 145 | +[rfc-3986]: https://tools.ietf.org/html/rfc3986 |
| 146 | +[targetRefs]: https://gateway-api.sigs.k8s.io/references/spec#gateway.networking.k8s.io/v1alpha2.PolicyTargetReference |
0 commit comments