SiYuan Has a Stored Cross-Site Scripting (XSS) Vulnerability via Unrestricted SVG File Upload
Moderate severity
GitHub Reviewed
Published
Jan 16, 2026
in
siyuan-note/siyuan
•
Updated Jan 16, 2026
Package
Affected versions
< 0.0.0-20260116101155-11115da3d0de
Patched versions
0.0.0-20260116101155-11115da3d0de
Description
Published to the GitHub Advisory Database
Jan 16, 2026
Reviewed
Jan 16, 2026
Published by the National Vulnerability Database
Jan 16, 2026
Last updated
Jan 16, 2026
Summary
A Stored Cross-Site Scripting (XSS) vulnerability exists in SiYuan Note. The application does not sanitize uploaded SVG files. If a user uploads and views a malicious SVG file (e.g., imported from an untrusted source), arbitrary JavaScript code is executed in the context of their authenticated session.
Details
The application allows authenticated users to upload files, including .svg images, without sanitizing the input to remove embedded JavaScript code (such as <script> tags or event handlers).
PoC

2. Create a file named test.svg with malicious JavaScript inside:
4. Open the file: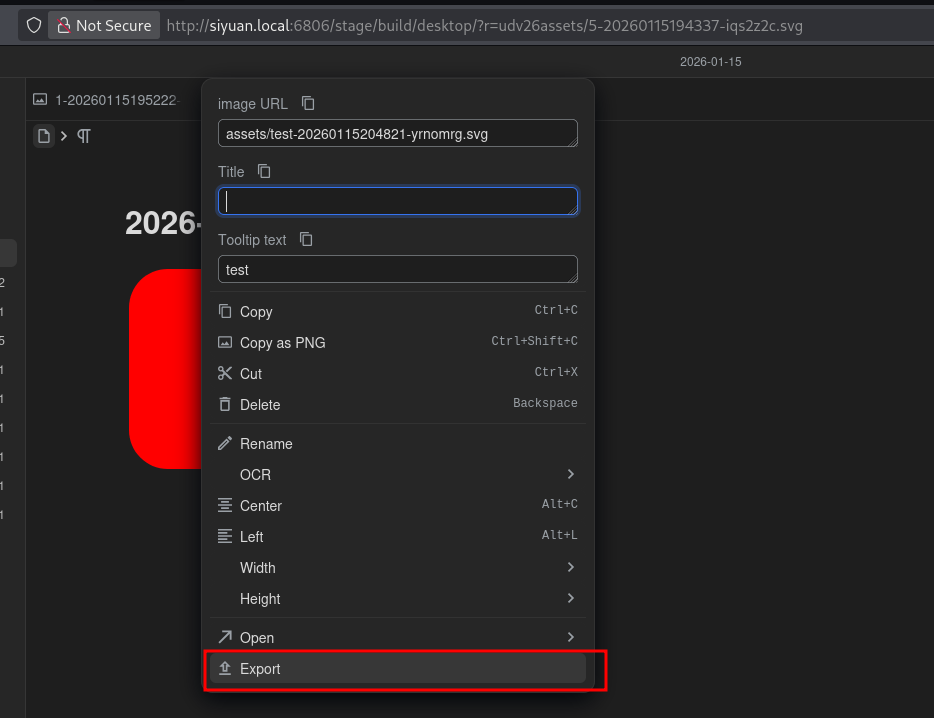
5. The JavaScript code executes immediately.Impact
The vulnerability allows to upload an SVG file containing malicious scripts. When a user exports this file, the embedded arbitrary JavaScript code is executed within their browser context
Notes
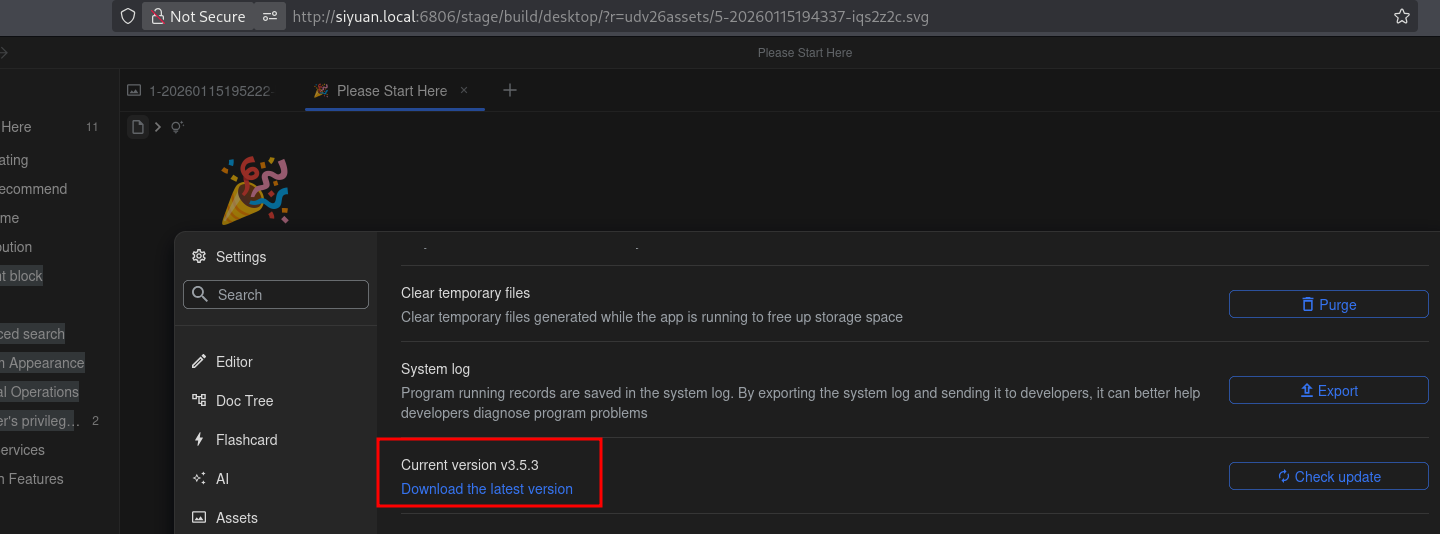
Tested version:
Solution
siyuan-note/siyuan#16844
References